First, the system design principle is to make the project intelligent security access control system to achieve advanced technology, economical and practical, safe and reliable, high quality requirements, adapt to the Internet + era, with access controller as the carrier, link IoT and other information platforms compatible Sex and scalability, the following principles should be followed in design:
Battery rechargeable Night Light comes in a variety of shapes and sizes. Some are designed to be used as emergency lights, while others are meant to provide a gentle illumination for your home or office. We are able to support all your needs for lighting.
Additionally, some models offer adjustable brightness levels, different color temperatures and timer functions that allow you to customize the amount of time that the light remains lit before it automatically shuts off after a certain period of time passes by.
We do a range of battery rechargeable night lights of cabinet lights, megnetic lights, table lamps, starry projector lights, etc.
Battery Charging Light, Charging Light, Chargeable Light, Wireless night light, Cordless Lights, Silicon Night Light Ningbo Deamak Star Intelligent Technology Co., Ltd , https://www.deamakstar.com
1. Advancement takes full account of the rapid development of the information society, and makes full use of the latest modern technology and the most reliable scientific and technological achievements in the case of investment costs, so that the technology is moderately advanced so that the system can be used for as long as possible. Adapt to social and technological developments and make the system have strong development potential.
2. Maturity and practicality Adopt technologies and products that have been proven to be mature and practical. In the equipment selection and system design, the needs of all employees' work, study, personal and property safety are maximized to ensure the adoption. The equipment is durable.
3. Scalability and integration In order to meet the needs of future development, the information involved in the entire intelligent security system must be fully considered. On the basis of satisfying the advanced nature and rationality, the overall structure has the characteristics of strong compatibility and expandability, and it is easy to upgrade and replace, ensuring that the whole system can be enriched, improved, improved and improved with the advancement and development of science and technology. .
4. Normative and structured Because the plant intelligent security system is very comprehensive, it is necessary to focus on the standards and specifications of all aspects in the overall design of the system, and strive to make the system structured, standardized and systematic.
5. Convenience All the channels of the factory are provided to employees or managers, and the flow of people is enormous. Therefore, the equipment used in the system should be convenient, fast, safe and reliable.
6. Economical and pertinent Under the premise of satisfying the practical, reliable and advanced system, according to the characteristics and requirements of the project itself, the highest cost performance is achieved in the system design, and the optimal design scheme is made.
Second, the project access control system introduction 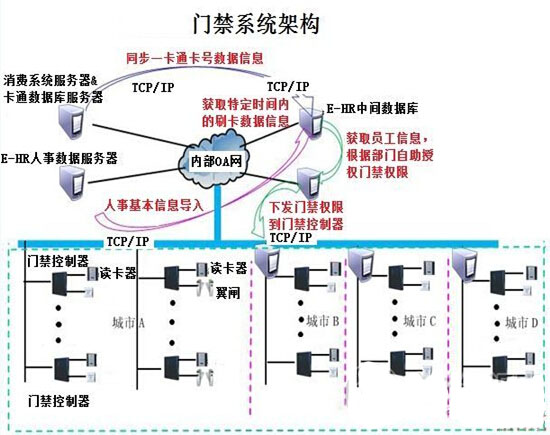
1) Adopt the latest TCP/IP network access control system: the main server of the access control system is set up by the city A base, and the city B, the city C, and the city D are connected by VPN to realize the transmission and sharing of information data. At the same time, the client workstations are set up in three places to connect with the access control main server of city A. The access control system clients of the four cities log in to the access control software through different rights accounts, and manage the access rights of their own areas;
2) The system is highly automated: the employee information of the access control system is synchronized with the information center database once a day to update the employee data. The access control synchronization software will filter the work number and synchronize it to the access control database, and bind permissions according to the department information. Group, automatic authorization to directly issue access control rights, no manual authorization, automatic authorization. Personalized manual authorization with special permission requirements;
3) It has two management modes: independent communication node and shared communication node, which is suitable for complex organizational management mode; according to project requirements and site conditions, the access control system is managed by shared communication nodes, and multiple zones are managed separately;
4) It has the management function of sub-organization organization: under the group, multiple organizations can be set up. According to the needs, the administrators of each organization can only manage the door points and set permissions of the organization, and can only view the card in and out of the institution. Event information, can not manage other institutions, the group's system administrator can manage all the doors and all personnel of the entire system;
5) Through a large-scale network card management system with multi-layer architecture, the organization can be a group, a company, a community, etc. Under which multiple nodes can be set up, the management capability is extremely strong, and one system can manage millions of access points. ;
6) The access control field controller saves the data of the card with authority on the controller. Under the offline state, it does not affect the card opening, and does not need to rely on the network real-time communication, which improves the running speed of the system;
7) Using MS SQL Sever as a database platform, using a multi-layer network structure, under the premise of supporting TCP/IP protocol, it can realize independent or mixed connection of RS485 and TCP/IP connection modes, which can satisfy both LAN and LAN. Wide-area network remote control, alarm and other functions, can run 24 hours a day, to ensure that users can see the latest monitoring information at any time;
8) Support multi-card opening mode: It can realize the function of opening up one access point after brushing up to 8 cards; also supports duress code to enter alarm and area anti-tracking function;
9) With anti-theft alarm function, the center can be disarmed, and the card can be swiped or password-disarmed at the scene;
10) The access control system has a voice alarm function of the control center;
11) The access control system can provide WebService interface to facilitate integration with other systems; it can provide comprehensive data interface, data dictionary, and dynamic link library for secondary development of users;
12) Automatically count the entry and exit of any person at any access point and at any time;
13) A variety of door mode states, which can set what state any of the access points are in at any time period;
14) Realize the management of the privilege of grading and time-sharing in designated areas, restricting the entry of outsiders into the company at will, and determining the prevailing level and the time allowed for passage according to the position or nature of the work, effectively preventing internal theft.
Third, the access control system commonly used equipment supporting type 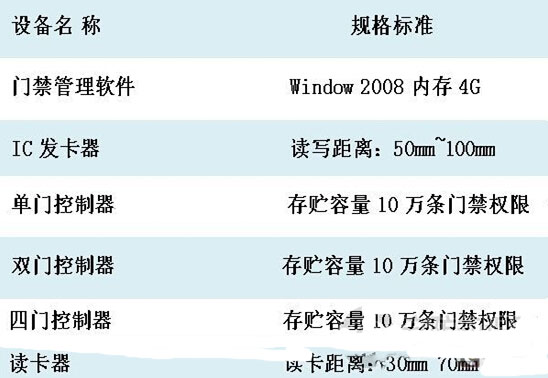
Advantages of the project access control system 1) Adopt international standard, TCP\IP digital technology effectively guarantees the advanced, reliable and compatible, no matter design, construction, installation, commissioning, or maintenance, it is easier and more standardized;
2) Universal network transmission equipment is convenient for procurement, installation, maintenance. The community networking part eliminates complicated intermediate equipment and reduces the investment of networking equipment;
3) The system supports multiple transmission protocols to ensure that the product can be fully compatible with the Ethernet networking mode, and the communication capability is strong, avoiding the phenomenon that the security information cannot be reported or missed in time due to communication congestion;
4) Intelligent access controllers can be divided into three types: one, two, four one-way swipe doors; all adopt the world's most advanced MOTOROLA micro control chip. MOTOROLA micro-control chip has the advantages of high speed, strong function and strong anti-interference. Built-in phase-locked module, can use 32KHZ crystal oscillator to generate frequencies up to 32MHZ, extremely effective in reducing interference and higher stability, storage capacity of up to 30,000 or so access control;
5) The core of the access controller device uses a 32-bit high-performance, low-power processor, 64M running memory, 64M storage space, and a storage capacity of 100,000 access permissions. The device supports remote upgrade, which facilitates the upgrade of the device.
V. Precautions for installation of the access control system 1) Do not install the access control system equipment in places where the sun is directly exposed to sunlight, high temperature, snow frost, chemical substances and dust;
2) Reader, the door open button is installed at a good visual level, should pay attention to the moderate height, easy to swipe;
3) It is strictly forbidden to operate during the installation process;
4) If the facade or wall is not flat during installation, apply glass glue to the gap to prevent dust or water from entering;
5) The main line of the system should be shielded, and the shield of the shield should be connected to the ground of the system, but not to the ground;
6) Separate the strong and weak electricity, keep the distance of 50cm or more with strong electric cables such as AC 220V, elevator line, cable TV line, etc. It is strictly forbidden to use the line pipe. The wire pipe of the wiring should be iron pipe as much as possible, and the two ends of the iron pipe should be connected to the ground below 3 meters deep to improve the anti-interference and lightning protection capability;
7) For the convenience of future maintenance and system stability, the wire ends of all networked wiring should not be placed inside the pipe and easily flooded, but should be placed outside the pipe and waterproof, so as to be inspected and maintained (the joint should be waterproof);
8) After all the connections are connected, it should be checked repeatedly and installed before being powered on;
9) The access card used in the access control system shall be kept magnetic, waterproof and anti-fold;
10) The surface of the sensor entry window used by the access control system should always be kept clean to enhance the reliability of the system identification information;
11) The access control host used for the first time should be cleared of the access control data before the setting to clear the access control data to initialize the memory.
VI. Conclusion Through the application case of the above access control system, it is the basic starting point for the user to meet the actual needs of the user, and to pursue high-quality product configuration according to the actual cost of the user. At the same time, in the construction process, it is necessary to reduce the intermediate links, reduce the unfavorable factors such as construction difficulty and complexity, adhere to the high starting point and high standard service concept of “professional protection, long-term careâ€, perfect the task and win the users. Good evaluation and praise.
1 time
Window._bd_share_config = { "common": { "bdSnsKey": {}, "bdText": "", "bdMini": "2", "bdMiniList": false, "bdPic": "", "bdStyle": " 0", "bdSize": "24" }, "share": {}, "image": { "viewList": ["qzone", "tsina", "tqq", "renren", "weixin"], "viewText": "Share to:", "viewSize": "16" }, "selectShare": { "bdContainerClass": null, "bdSelectMiniList": ["qzone", "tsina", "tqq", "renren" , "weixin"] } }; with (document) 0[(getElementsByTagName('head')[0] || body).appendChild(createElement('script')).src = 'http://bdimg.share. Baidu.com/static/api/js/share.js?v=89860593.js?cdnversion=' + ~(-new Date() / 36e5)];