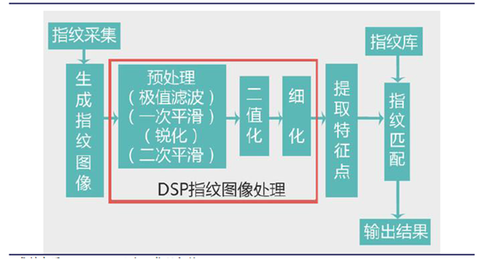
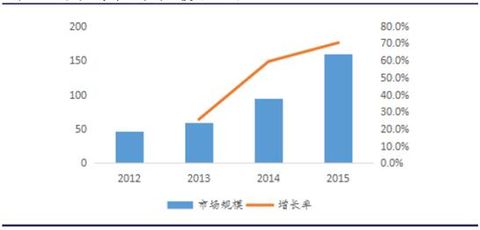
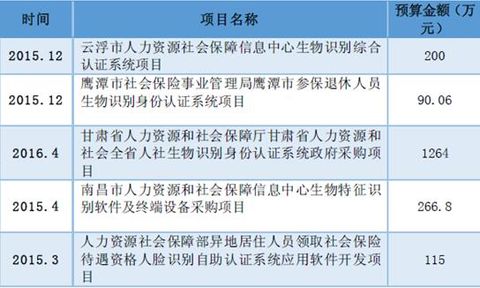
HC Security Network News recently, First Research Institute of Ministry of Public Security announced on the National Cyber Security Awareness Week 2016 activities, developed their own "network trusted identity authentication service platform" will be put into pilot and more. 1. From the online copy of the ID card, biometrics is on the rise. Recently, the First Institute of the Ministry of Public Security released a message at the 2016 National Cyber ​​Security Publicity Week. The “Network Trusted Identity Authentication Service Platform†developed by the Ministry of Public Security will soon be put into trials in many places. Through this platform, individuals can generate a lifetime ID number of “ID card online copy†on the Internet. In the future, it is not necessary to carry an ID card. When you check in hotels, open online stores and other businesses that require real-name authentication, you can complete it by “brushing your faceâ€. Identity authentication while avoiding the risk of identity being spoofed. The technical principle of face recognition is face recognition in biometrics. The so-called biometric technology is the combination of computer and optical, acoustic, biosensor and biostatistical principles, using the inherent physiological characteristics of the human body (such as fingerprints, faces, irises, veins, etc.) and behavioral characteristics ( Such as voice, gait, etc. to identify the identity of the individual. Since the human body features the inherent non-reproducibility of the human body, this biometric key cannot be copied, stolen or forgotten, and biometric identification technology is used for identity identification, which is safe, reliable and accurate. Common passwords, IC cards, stripe codes, magnetic cards or keys have many disadvantages such as loss, forgetting, copying and theft. In addition, biometric technology products are realized by means of modern computer technology, and it is easy to cooperate with computers and security, monitoring, management system integration, and achieve automatic management. For a long time, insufficient technological innovation, limited application and high price and high cost are the three major factors that restrict the development of biometrics in China. In terms of technology, the original innovation of biometric sensors and core algorithms is insufficient, and the technical standards are not well developed. On the application side, biometrics are basically limited to access control attendance, bank internal control, and public security departments' entry and exit management and criminals. To personal consumption; in terms of price, lack of market competition and immature technology lead to high prices. However, in recent years, this situation has begun to turn, and the three major problems are gradually being resolved. Technology: The maturity of deep learning algorithms has led to a significant increase in the accuracy of biometrics. Advances in computer technology based on deep learning algorithms provide powerful computational and analytical tools for biometrics. In turn, the huge amount of biometric data also provides a wealth of material for machine training, "big data becomes the fuel of artificial intelligence." Face recognition, Face++ team created the world's highest face recognition accuracy rate, has been in the face detection FDDB evaluation, face key point positioning 300-W evaluation and face recognition LFW evaluation, won three consecutive World number one. In terms of fingerprint identification, domestic manufacturers such as Mindray, Aegis, and Weier Technology already have fingerprint recognition autonomic algorithms and core patents. In addition, third-party fingerprint identification algorithm providers such as Hangzhou Qianyuan and Shenzhen Zhixin have emerged. . In terms of iris recognition, Tiancheng Shengye has launched the world's smallest iris recognition module, which can realize natural iris recognition by using a module to achieve natural reading distance (7-30cm). In terms of vein recognition, the School of Electronic Science and Engineering of National University of Defense Technology has successfully developed a vein identification security system. Application: At present, the application scenarios of biometrics have been greatly expanded. The bank applies biometric identification in the customer identity verification scenario, covering different risk level scenarios such as weak real-name electronic account opening, settlement account opening and deposit and withdrawal. Mobile payment applications such as third-party payments and mobile banking have begun to use biometrics. The public security department has vigorously introduced technologies such as fingerprints and face recognition in video surveillance and personnel access management in various types of places. Under the policy push, biometrics has also been placed in the social security, education, and medical systems. In recent years, domestic smart phone consumption has increased dramatically, mobile phone users' mobile payment habits have gradually developed, and smart homes have become popular. The growth of personal consumption demand in the three aspects has pushed consumer-grade fingerprint recognition on the mobile phone to begin to break out, and the iris has gradually entered. Price: In terms of fingerprint identification, the price of fingerprint recognition module has been declining in the past two years. In terms of face recognition, Hanwang’s 500-person face recognition attendance machine cost more than 4,000 yuan when it was first introduced in 2009. It was reduced to about 3,000 yuan when the second generation was launched in 2010. Dropped to around 2,700 yuan. Benefiting from the gradual solution of the three major problems, the domestic biometrics industry is welcoming unprecedented development opportunities, and its application scope and market size are expected to achieve rapid expansion. 2. Preliminary study on biometric technology 2.1, the minimum system and basic working process of biometric identification Typically, a biometric minimum system consists of three parts: Sensor, memory, and processor. The sensor is the collection mechanism of the user's biological information; the processor is responsible for information preprocessing, feature extraction, feature training, feature matching and feature recognition; the memory is responsible for feature extraction and storage of training results. The biometric work process includes two stages: user registration and identity authentication. The process mainly includes four steps: biometric collection, preprocessing, feature extraction and pattern recognition: 1) Feature collection Feature acquisition is the process of using sensors to convert the inherent physiological characteristics of the human body into computer-readable digital information. The biometric sensor mainly uses high-precision optical devices such as scanners and cameras, as well as crystal sensor chips based on capacitance and electric field technology, ultrasonic scanning, and infrared scanning. 2) Pretreatment Preprocessing is the process of normalizing the digital information read by the sensor and processing the raw data into semi-structured data. Generally, preprocessing methods mainly include information compression, noise reduction, and data normalization. 3) Feature extraction Feature extraction is the most representative part of extracting biometrics and is the process of converting it into structured data. Feature extraction and expression are the key points and difficulties of the biometric recognition process. For example, iris, fingerprint, face and other images are prone to uneven illumination, plane rotation, partial occlusion and three-dimensional deformation. This brings great obstacles to subsequent feature matching and pattern recognition, which may lead to recognition failure and failure to identify. 4) Pattern recognition Pattern recognition usually includes feature training, feature matching and feature recognition. It is a process of constructing classifiers through machine learning and data mining to match and identify structured feature vectors. Among them, the feature training is to learn the biometric data set collected by the user registration stage through the machine learning method to generate the biometric classifier model; the feature matching is the biometric database model generated by the biometrics extracted during the identity authentication phase and the user registration phase. Matching is performed, and the similarity between the two is calculated; the feature recognition sets the identification criteria such as the similarity threshold, and accepts or rejects the recognized result. 2.2. Analysis of six types of biometrics At present, the main mainstream of biometrics are fingerprints, face, iris, vein, voiceprint, and gait recognition. This chapter will briefly introduce their respective technical principles, technical features and current development stages. Fingerprint recognition Automatic Fingerprint Identification System (AFIS) is the earliest and most mature biometric technology used in pattern recognition. It integrates sensor technology, biotechnology, electronic technology, digital image processing and pattern recognition. Figure: Sketch of the fingerprint identification system In general, the AFIS system consists mainly of the following components: (1) Fingerprint image input Fingerprint images are acquired in the AFIS system in two ways, optical scanning acquisition and solid-state sensor acquisition. Optical scanning capture fingerprint images generally use total reflection technology (FTIR). When the finger is placed on the prism, the ridge of the finger contacts the prism and the valley does not contact the prism. The laser illuminates the prism at a certain angle to generate total reflection, and the CCD array receives and acquires the fingerprint image. When the solid sensor captures an image, the voltage of the capacitor is changed by the finger on the surface of the sensor to acquire an image. Compared with optical scanning, solid-state sensors have the characteristics of small size, high integration, digitization, etc., but the acquisition range is small, and optical scanning is rarely limited in the acquisition range. (2) Fingerprint image enhancement There are many kinds of feature definitions of fingerprint images. The definition of the most commonly used detail features is the detailed model proposed by the American FBI. It divides the most salient features of the fingerprint image into ridge end points and bifurcation points. Each clear fingerprint typically has 40 to 100 such details. The performance of the detail feature extraction algorithm depends heavily on the quality of the input fingerprint image. In order to ensure the performance of the detail feature algorithm, the fingerprint image enhancement needs to be performed first before extracting the feature. The purpose of fingerprint image enhancement is to improve the sharpness of the ridge information of the recoverable area while deleting the unrecoverable area. In general, image enhancement is performed using digital image processing methods such as smoothing, filtering, binarization, and refinement. (3) Fingerprint image feature extraction Matching two fingerprint images largely adopts a method based on comparing dot patterns of two fingerprint images. The points used for matching can be divided into two categories: minutiae points and individual points. The points used to match the fingerprint image are called minutiae points, which are the ridge end points and bifurcation points in the fingerprint image topology. Individual points include center points and triangle points, and the distance between them and the number of ridge lines are generally considered not to change with image transformation, rotation, magnification, and reduction. Therefore, this feature is often used to reduce the search space of the database at the time of matching. (4) Fingerprint image matching Fingerprint image matching is to determine whether the feature set (template) of two input fingerprints belongs to the same fingerprint. There are many methods for fingerprint matching algorithms, including image-based matching, ridge pattern matching, point pattern matching, and graph-based matching. Although the fingerprint identification technology is mature and the cost is relatively low, there are still shortcomings such as being easily forged, having low precision, poor concealment, and being easily affected by the state of the examiner and the environment. Ultrasonic sensors have also been used to acquire images, which are acquired using ultrasonic reflection ranging. Ultrasonic fingerprint technology can be scanned through a smartphone case made of glass, aluminum, stainless steel, sapphire or plastic. The scan can be protected from dirt that may be present on the finger, such as sweat, hand cream or condensation, providing a more stable and accurate method of authentication. In addition, the ultrasound-based solution uses sound waves directly across the surface of the skin to identify three-dimensional details and unique fingerprint features that are currently unrecognizable by capacitive touchscreen-based fingerprinting techniques, including fingerprint ridges and sweat pores. This produces a fingerprint surface map that is rich in detail and difficult to copy. Face recognition Face recognition technology is a kind of biometric recognition technology based on human facial feature information, including face image acquisition, face location, face recognition preprocessing, identity confirmation and identity search. The technology combines knowledge and related technologies in biology, psychology, cognition, pattern recognition, image processing, computer vision, etc. It can be widely used in identity verification, identity authentication, access control, security monitoring, and human-machine exchange. Scenes. The engineering application of face recognition began in the 1960s. After more than 50 years of development, face recognition technology has made major breakthroughs, and many classic algorithms and face libraries have appeared one after another. At present, the highest correct rate of face recognition system can reach 99.5%, and the correct rate of recognition of human eyes under the same conditions is only 97.52%, and the accuracy of face recognition has been more accurate than the naked eye. At the same time, with the development of high-performance computers, many automatic identification systems for machines have been introduced at home and abroad, prompting face recognition technology to enter the practical stage. The more successful commercial face recognition systems in foreign countries include FaceIt developed by Identix, AcSysFRS of AcSys, and EPL of EyeMatic. China's face recognition technology ranks first in the world. At present, the world's highest face recognition accuracy rate is created by our Face++ team. At the same time, due to the special national conditions of China's large population base, the government and industry have more urgent needs for face recognition technology, which promotes the commercialization process of face recognition in China, and the face recognition technology and products have been applied to the government. , military, banking, social security, e-commerce, security and other fields. Compared with other biometrics, face recognition technology has unique technical advantages in practical aspects, mainly reflected in the following aspects: 1. Non-contact: The collection of face images is different from fingerprints and palm prints. It is necessary to contact the palm-grain collection equipment. The collection of palm prints is not hygienic except for certain wear and tear on the equipment. The device for collecting face images is a camera and does not need to be touched. 2, non-intrusion: the collection of face photos can be automatically taken using the camera, without the need for staff intervention, and does not need to be matched by the collector, just in front of the camera through the normal state. 3. Friendly: A human face is a biological feature that is exposed after a person is born, so its privacy is not as strong as palm prints and irises, so the collection of faces is not as unacceptable as the palm print collection. . 4, intuitive: We judge who is a person, by looking at this person's face is the most intuitive way, unlike the palm print, iris and other related fields experts can be judged. 5, fast: the face collection from the camera surveillance area is very fast, because its non-intervention and non-contact, the face acquisition time is greatly shortened. 6, simple: face acquisition front-end equipment - camera can be seen everywhere, it is not a dedicated device, so easy to operate. 7. Scalability is good: its collection end can completely adopt the camera equipment of the existing video surveillance system. The scalability of the back-end application determines that face recognition can be applied to access control, blacklist monitoring, face photo search, etc. field. Iris recognition Each iris contains a unique structure based on features such as crowns, crystals, filaments, etc. No two irises are the same. Iris recognition technology uses the characteristics of iris lifetime invariance and difference to identify identity. The iris recognition system is mainly composed of iris image acquisition, image preprocessing, feature extraction, feature matching, and conclusion. (1) Acquisition of iris images: The primary task of iris recognition is to obtain high-quality iris images, which is one of the most difficult technologies for iris recognition. Since the iris is distinguished mainly by the difference in texture details, and the texture of the iris is not very clear, especially for yellow people, it is difficult to obtain a clear iris image with a normal CCD camera and under normal lighting conditions. There are currently two representative iris image ingesting devices. One is to adjust the LED light source, and the digital camera captures an eye image with a resolution of 256×256 pixels from a distance of 30 to 50 cm. The other is a small portable opto-mechanical device, the upper end of the device casing is fastened to the subject's eyes, and under the illumination of the infrared emitting tube and the light-emitting diode, the iris image is collected by the CCD camera and input into the computer. (2) Iris image preprocessing: Preprocessing is a prerequisite for effective feature extraction and feature matching. Its main task is to separate the iris image from the image of the ingested eye. For example, adaptive Wiener filtering is used to remove the noise interference due to reflection, localization of the iris image by histogram equalization, accurate positioning of the inner and outer edges of the iris by Hough transform, and drift elimination by translation and image alignment. , scaling, and rotation to make the iris image structure consistent. (3) Feature extraction: Iris feature extraction uses complex two-dimensional Gabor wavelet to decompose the iris image. (4) Feature matching: After obtaining the encoding of the iris image, it is necessary to identify the encoding to identify the authenticity of the identity. There are many algorithms for image matching technology, such as correlation function measurement algorithm, correlation coefficient measurement algorithm, and hierarchical search decision algorithm. In general, iris recognition has extremely high accuracy. If the threshold is set to be reasonable, the false recognition rate of iris recognition is almost zero, and it is extremely difficult to forge, and has good living body recognition characteristics. However, there are still problems such as expensive equipment, difficult collection, and the technology is not yet fully mature. Vein recognition Vein recognition technology is a biometric recognition technology. It uses the hemoglobin in human venous blood to absorb light from near-infrared light. Through vein recognition algorithm, it realizes the identification of human beings, which is safe and reliable, and has high recognition accuracy. The most common sites of vein recognition include the finger vein and the palm vein. From the technical system, vein recognition mainly includes four stages: image acquisition, pretreatment, feature extraction and matching. Firstly, the blood flowing in human veins can absorb the characteristics of specific wavelengths of light, and use specific wavelengths of light to specific parts. The irradiation is performed to obtain a clear image of the vein at the relevant site, and the acquired image is analyzed and processed to obtain the biological characteristics of the vein at the specific site, and the obtained vein characteristic information is compared with the previously registered vein feature to confirm the identity of the registrant. In terms of safety, the uniqueness of living recognition and vein characteristics makes vein recognition a significant advantage. Since the venous blood vessels are hidden in the human body and the hemoglobin is stored in the venous blood vessels, only blood circulation can provide hemoglobin activity, which is recognized and thus difficult to be copied and stolen. At the same time, for adults, their left and right hand veins are completely different. The vein pattern will not change with age. Even twins will not have the same vein pattern, and the unique characteristics of veins are very strong. In terms of accuracy, vein recognition is one of the most recognized biometric methods. The internal sample collected by near-infrared irradiation is less affected by the external environment, and the recognition rate is high. After rigorous testing by the medical profession, the rejection rate of vein recognition technology is less than 0.01%, the false alarm rate is less than 0.0001%, and the login failure rate is 0%. The accuracy ranks among the top of other biometrics. Although the vein identification has the advantages of safety and accuracy, the current vein identification is limited by its own characteristics, and the product is difficult to be miniaturized. It has special requirements for the collection equipment, the design is relatively complicated, and the manufacturing cost is high. Taken together, in the more common biometrics, fingerprints, faces, and irises are three of the more successful applications. Among them, fingerprint recognition has been widely used due to its low cost and low threshold for collection. The application, face recognition is gradually popularized with the maturity of image recognition technology; iris recognition accuracy is extremely high, but due to high cost, high collection threshold, application scenarios are limited. Vein recognition has also become more and more widely used with the continuous advancement of technology, and in some cases, the replacement of fingerprint recognition is realized. Voiceprint recognition The organs used by people in speaking differ greatly in size and shape, so the voiceprints of any two people are different, and for everyone, from the development of the teens to the fifties, Its voiceprint remains basically unchanged. Voiceprint recognition technology makes use of this feature to input sound into the sonograph, so that the mechanical vibration of different frequencies of the sound becomes a spectrum image, displayed on the screen or recorded on paper. This image is the voiceprint. The working process of the voiceprint recognition system can generally be divided into two processes: the training process and the recognition process. First, the input raw speech signal needs to be preprocessed, such as sampling, quantization, pre-emphasis, and windowing. In the training process, the voiceprint recognition system should learn the training of the extracted speaker's voice features, establish a voiceprint template or a voice model library, or adapt the existing voiceprint template or voice model library in the system. . In the recognition process, the voiceprint recognition system should perform pattern matching calculation on the characteristic parameters of the input voice according to the existing voiceprint template or voice model library of the system, thereby realizing recognition and judgment and obtaining the recognition result. Beginning with the rapid development of computer technology in the late 1970s, the research on voiceprint recognition turned to nonlinear processing of various acoustic characteristic parameters and new pattern matching methods. In the aspect of feature parameter extraction technology, nonlinear processing methods such as wavelet feature parameters and linear prediction combinations of different feature parameters have been proposed and widely used. In recent years, the adoption of DSP chip computing technology has enabled the current speech feature parameter extraction technology to reach a relatively mature stage. In the aspect of pattern matching judgment technology: from the beginning of the 1980s, the hidden Markov model, artificial neural network and other technologies have been effectively utilized in voiceprint recognition, and gradually become the mainstream pattern matching method of voiceprint recognition system; After the 1990s, Gaussian hybrid model technology has quickly become an important voiceprint recognition technology due to its simplicity, effectiveness and good robustness. Since the 21st century, the support vector machine technology and the fusion of multiple pattern matching methods have also been deepened. Research and development, and entered the practical stage of commercialization. Compared with other biometric technologies, voiceprints are simple, accurate, economical and scalable. Compared with other biometric technologies, voiceprints have many advantages such as simplicity, accuracy, economy and scalability. Of course, voiceprint recognition technology is also There are some technical difficulties. For example, there are some technical difficulties in using very short voices, such as: training and recognizing models with very short voices, effectively distinguishing models from training and recognition by realizing the elimination or attenuation of changes. Effectively distinguishing the imitation sounds to truly eliminate or attenuate the effects of changes; eliminate channel differences and background noise. Gait recognition Gait refers to the posture of people walking, a kind of biological behavior characteristics that can be perceived at a long distance, and identity authentication with gait characteristics is a research hotspot in the field of computer vision and biometric identification in recent years. Gait recognition is to analyze the image sequence containing human motion, usually including gait detection, and the analysis is to analyze the image sequence containing human motion, usually including gait detection, gait characterization and gait recognition. 3 processes. Gait detection is the extraction of the human gait contour area from the background image in the image sequence. Research in this area includes background estimation, target detection, and post-morphological processing. Effective segmentation of gait contour regions is very important for post-processing such as feature extraction and target classification. Therefore, gait detection is often regarded as a preprocessing part of gait recognition. Gait characterization is a way to represent the detected gait and the known gait in the database, also known as gait feature extraction. Gait recognition refers to comparing the gait information to be identified with the gait characteristics in the database, and determining the category to which it belongs by a certain judgment basis. There are template matching methods, state space methods, and so on. The advantages of gait recognition are non-contact, non-invasive, easy to perceive, difficult to hide, and difficult to disguise. Based on these advantages, gait recognition has broad application prospects and economic value in the fields of access control systems, security monitoring, human-computer interaction, and medical diagnosis. Compared with other biometric technologies (such as fingerprints, faces, irises, etc.), the benefits of data availability and non-contact detection, voiceprint recognition and gait recognition have their own unique advantages, so The field has high application value. 3, commercial-grade applications: deep accumulation, new technology and new scenes drive new markets 3.1, access control: fingerprint application is wide, the face is mature Fingerprint recognition is the most widely used, low-cost, and easy-to-use biometric technology in access control systems. However, fingerprints are the texture of the epidermis after all, the capacity is subject to changes due to external factors, and it is easy to be forged. In industries with high security requirements, fingerprint identification products will be limited to some extent. The new generation of access control products that embed face recognition products into the access control system are becoming more and more mature. At present, the face recognition access control system is mainly used in places with high security requirements, such as prison access control and bank vault. In addition, in recent years, technologies such as iris and vein recognition have also begun to be applied to access control systems. In 2011, CSIC 710 successfully developed a finger vein identification access control system. Figure: Market size of domestic access control system (100 million yuan) In recent years, smart communities and banks, smart city security and other projects have promoted the rapid growth of the access control market. The growth rate has been increasing in the past three years. In 2015, the market scale reached 16 billion yuan. With the increase in the penetration rate of overlay biometrics in the access control market, biometrics will achieve rapid growth. 3.2, attendance: fingerprints in the road, face realization technology breakthrough Applying biometric technology to the employee's attendance system can help solve the problem of the traditional punching card and the C card attendance method, ensure the attendance data is true, and improve the efficiency and quality of the enterprise staff management. Among all biometric technologies applied to attendance machines, fingerprints account for the largest share. In addition, with the further application of 3D live fingerprint recognition technology in products, the use of fingerprint film generation, fingerprint skin environment abnormalities lead to pattern recognition difficulties, slow recognition speed, causing several problems of queuing attendance will be alleviated, 3D fingerprint attendance machine will To some extent, the replacement of the traditional optical fingerprint recognition attendance machine is realized. Through the attendance of some unique feature recognition tests on the face, the current technical level has broken through the influence of day and night light, and can achieve rapid recognition under natural conditions. Compared with fingerprint recognition, face recognition completely eliminates the occurrence of card attendance and eliminates the embarrassing situation of fingerprint attendance contact. Iris recognition technology was widely used in the coal industry for attendance at an early stage. At present, the application of iris recognition technology to the building real-name system management system has been promoted nationwide, and the cases in Zhuhai and Guiyang are more prominent. The vein recognition attendance system has also been applied in some enterprises and universities. 3.3. Application in the financial industry: deepening bank customers, mobile payment inciting incremental market Financial institutions have extremely high requirements for security. Therefore, biometric identification technology is first widely used in the internal control of banks. The bank's confidential information safe, treasury access control, and teller business authorization basically adopt biometric technology. In May 2013, Everbright Bank introduced a fingerprint identification unified identity authentication platform, and replaced fingerprints with fingerprints to log in to the bank's internal business system such as the core business system and the inspection system. From weak real-name electronic account cards to deposits and withdrawals, biometrics expands to higher-risk bank customer identification scenarios. In December 2015, in order to improve personal banking settlement account services, the People's Bank of China issued the “Notice of the People's Bank of China on Improving Personal Bank Accounts to Strengthen Account Managementâ€. The "Notice" clearly proposes to expand the account opening channel and increase the remote account opening channel. The qualified banks can explore the biometrics technology and other safe and effective technical means as the verification of the identity information of the account opening applicant. Clear government and other safe and effective technical means as an aid to verify the identity of the applicant. Clear policy support further promotes the biometrics technology in the bank customer identity verification scenario into the practical phase. Figure: China Merchants Bank brush face withdrawal As early as 2014, Jiangsu Bank launched the “brush face†technology in all physical outlets under the jurisdiction, mainly for assisting account opening, network verification and portrait comparison. After years of development, three types of technologies, including face recognition, vein recognition, and voiceprint recognition, have already landed. Face recognition is currently the most widely used, and is mainly used for identity verification when a weak real-name electronic account (such as a direct bank account) is opened. Weak real-name electronic accounts cannot be paid, transferred, cashed, or exchanged, so the application of biometric technology is less risky. For example, it belongs to the weak real name electronic account direct bank account, its function is limited to the purchase of this and the card issuance and distribution of the balance of wealth management products, funds can only go through the binding bank settlement account. In addition, face recognition technology has also been used to assist inbound and outbound accounts only through the bound bank settlement account. In addition, face recognition technology has also been used to assist the household's nuclear body opening, mobile phone bank account opening, credit card application also uses face recognition technology. With the opening of the merchant's nuclear body, mobile banking and credit card applications have also enabled face recognition technology. With the launch of the face-lifting business in 2015, China Merchants Bank officially entered the identity verification scene when depositing and withdrawing money. Vein recognition has been applied to the deposit and withdrawal business of a number of bank self-service devices, and voiceprint recognition has been first applied in the mobile banking login verification service of CCB. Mobile payments open a huge incremental market. At present, the most widely used and best-selling technology is fingerprint recognition. Third-party mobile payment tools such as Alipay and WeChat and mobile banking of many banks have launched fingerprint direct payment functions. In September 2015, CITIC Bank cooperated with Huawei to launch fingerprint recognition near-field payment. MateS Huawei Wallet APP is bound to CITIC Bank Credit Card, which can open the same amount of electronic credit card online. Users can finish the mobile phone on UnionPay POS machine. Screen payment. “Out-screen payment†means that when the user closes the account, he only needs to hold the mobile phone close to the POS machine, and then the screen can be cancelled to evoke the payment page, and the fingerprint verification can complete the small payment within 200 yuan; if the consumption amount exceeds 200 yuan, Simply type the credit card password on the POS machine to complete the payment. Recently, Minsheng Bank launched the first iris payment in the industry. Face recognition technology has been proposed for a long time, but it has not yet landed in third-party mobile payment tools. Voiceprint recognition has not yet been put into practical use. Compared with the authentication of bank customers, the application of biometrics in mobile payment scenarios is still in its infancy. At present, only fingerprint payment has achieved a wide range of landings. According to TrendForce, the global mobile payment market in 2015 was US$450 billion, and it is estimated that it will reach US$620 billion in 2016, with an annual growth rate of 37.8%. In 2015, the number of online mobile payment users in China reached 358 million, with a growth rate of 64.5%, which was 1.8 times the growth rate of users in the overall online payment market. The proportion of online payment for mobile phone users increased from 39.0% to 57.7%. With the further improvement of fingerprint recognition penetration rate and the landing of technologies such as face recognition and iris voiceprint, biometric technology will open a huge incremental market in mobile payment applications such as third-party payment instruments and mobile banking. In 2009, the application of Chinese business in the biometrics industry segment accounted for 84.9% (calculated by sales). (calculated by sales). If this ratio remains unchanged, according to the forecast of China's 2020 biometric market size of 30 billion yuan, the market size of commercial-grade applications will reach 25.47 billion yuan. 4. Government and public-level applications: initial scale, multi-policy support to stabilize the market 4.1, public security department: intelligent monitoring + personnel access management to help face recognition lead This year, the public security department achieved a number of projects in the field of bio-identification focused on monitoring and personnel access management. In many technologies, face recognition is the leader. Face recognition promotes the development of video surveillance to intelligence. With the advancement of the construction of safe cities, many cities in China have deployed a large number of security surveillance cameras. The resulting massive video data brings opportunities for public area security and also poses great challenges. Fully relying on manual monitoring or troubleshooting, can not meet the needs of practical applications, the integration of face recognition technology into video surveillance systems, improve the level of intelligent analysis of video surveillance, is an effective way to meet the challenges. This year, Hefei opened the face recognition “Tianwangâ€. All the trains and bus stations in Hefei have face recognition devices. All the passing people will be captured by the system to collect facial information, and collected and stored in the library. When the case occurs, Hefei's security video surveillance alarm system can record the suspect's appearance into the library for retrieval and find a matching face. Face recognition began to be used for personnel access management in many types of places: In July this year, Shenzhen Airport became the first airport in the country to embed the face recognition system into the airport security information system and realize the integrated operation of the two systems. The first domestic airport security screenings No.7 and No.8 were embedded in the system. In the past month, the system found 10 passengers who used the fraudulent documents. The airport security checkpoint recently seized nearly 30% of the total number of such passengers. It has shown strong professionalism and practicality in improving the on-site inspection capability and effectively screening passengers for fraudulent use of documents. It can effectively prevent the illegal elements from changing the boarding pass and then deliberately exchange the boarding pass to board the security check hole of the other aircraft. . In September this year, the Nanjing traffic police used face recognition technology for the first time. Since the face recognition system was launched, the public security checkpoint has inspected 3,200 people and found 32 people with problems, including ID card expiration, inconsistency, and 2 The fugitive and two drug addicts were captured. 2014年,公安部部级的生物识别采è´é‡‘é¢ä¸º819.2万元,2015年采è´é‡‘é¢ä¸º899.78万元,而今年截æ¢åˆ°çŽ°åœ¨ï¼Œé‡‡è´é‡‘é¢å·²è¾¾1471.08万元。如果地方公安机关的采è´é¢èƒ½å¤Ÿå®žçŽ°ç›¸ä¼¼çš„增速,生物识别将在公安行业将迎æ¥ç¿»å€å¢žé•¿ã€‚æ¤å¤–,公安部部级近三年的采è´é¡¹ç›®åŸºæœ¬éƒ½æ˜¯äººè„¸è¯†åˆ«é¡¹ç›®ï¼Œå¯¹äºŽå…¶ä»–生物识别技术,仅在今年采è´äº†236万元的ç¾è¯æŒ‡çº¹é‡‡é›†ä»ªç¡¬å¤‡ã€‚å¯è§ï¼Œäººè„¸è¯†åˆ«çŸæœŸå†…将主导市场的增长。 4.2ã€ç¤¾ä¿éƒ¨é—¨ï¼šç”Ÿç‰©è¯†åˆ«æ£å¼å…¥é©»ç¤¾ä¿ç³»ç»Ÿ 2015年,人社部æ出è¦ç´§å¯†è·Ÿè¸ªèŠ¯ç‰‡æŠ€æœ¯çš„å‘展方å‘,积æžç ”ç©¶æ— çº¿æ”¯ä»˜ã€åŸºäºŽäº’è”网æœåŠ¡çš„用å¡æ–¹å¼ã€ç”Ÿç‰©ç‰¹å¾è¯†åˆ«ç‰æ–°æŠ€æœ¯çš„应用,为新一代社会ä¿éšœå¡åšå¥½æŠ€æœ¯å‚¨å¤‡ã€‚ç”±æ¤ï¼Œç”Ÿç‰©è¯†åˆ«æŠ€æœ¯æ£å¼å…¥é©»ç¤¾ä¿å¡ã€‚社ä¿ç”Ÿç‰©è¯†åˆ«ç³»ç»Ÿçš„基本结构和工作过程如下: 1)特å¾é‡‡é›†ï¼šå‚ä¿äººåœ¨ç³»ç»Ÿä¸æ³¨å†Œï¼Œå¡«æŠ¥æœ¬äººçš„身份è¯ã€å¹´é¾„ã€åœ°å€ã€æ‰€å±žå•ä½ç‰åŸºæœ¬ä¿¡æ¯ï¼Œè®¾ç½®æœ¬äººçš„系统登录密ç 并采集生物特å¾ä¿¡æ¯ï¼›ç³»ç»Ÿå°†æ‰€æœ‰ç”¨æˆ·ä¿¡æ¯å’Œå…¶å¯¹åº”的生物特å¾é›†ä¸å˜å‚¨äºŽæ•°æ®åº“ä¸ã€‚ 2)认è¯ï¼šå‚ä¿äººå®šæœŸä½¿ç”¨å¯†ç 或身份è¯ç™»å½•ç³»ç»Ÿï¼Œå¹¶è¿›è¡Œç”Ÿç‰©ç‰¹å¾è®¤è¯ï¼Œä»¥ç¡®å‚ä¿äººçš„身份和生å˜çŠ¶æ€ï¼›ç³»ç»Ÿåˆ™æ ¹æ®ç”¨æˆ·æ供的登录信æ¯æå–其生物特å¾è¿›è¡ŒåŒ¹é…验è¯ï¼Œè®¤è¯è¿‡ç¨‹ä¸å¯ä»¥å½•åƒä¿å˜éªŒè¯èµ„料。 < 3)社会ä¿é™©ä¿¡æ¯ç³»ç»Ÿä¾æ®è®¤è¯èŽ·å¾—的身份和生å˜ä¿¡æ¯å†³å®šå¦‚何进行社会ä¿é™©çš„å‘放。 年以æ¥ï¼Œå„级人社部门对生物识别的采è´åŒ…括了人脸识别ã€é™è„‰è¯†åˆ«å’ŒæŒ‡çº¹è¯†åˆ«ä¸‰ç±»æŠ€æœ¯ã€‚æ ¹æ®ä¸‹è¡¨æ•°æ®ï¼Œæˆ‘们å‡è®¾æ¯ä¸ªå¸‚的采è´é‡‘é¢ä¸º200万元。按国内共计293个地级市计算,市级人社部门的生物识别市场约为5.86亿元。åŒæ—¶ï¼Œå‡è®¾çœçº§é‡‡è´é‡‘é¢ä¸º1200万元(甘肃çœ2016年采è´é‡‘é¢ä¸º1264万元),按国内共计32个çœå’Œè‡ªæ²»åŒºè®¡ç®—,çœçº§äººç¤¾éƒ¨é—¨çš„生物识别市场约为3.84äº¿å…ƒã€‚åŠ æ€»ä¹‹åŽå…¨å›½äººç¤¾éƒ¨é—¨ç”Ÿç‰©è¯†åˆ«å¸‚场的空间约为9.7亿元。 表:å„级人社部门部分生物识别采è´é¡¹ç›® 4.3ã€æ•™è‚²éƒ¨é—¨ï¼šå„类考试有望æå»ºæ–°å…¥å£ 2016å¹´2月29å·ï¼Œæ•™è‚²éƒ¨å‘布了《关于åšå¥½2016å¹´æ™®é€šé«˜æ ¡æ‹›ç”Ÿå·¥ä½œçš„é€šçŸ¥ã€‹ï¼Œé€šçŸ¥ä¸æ•™è‚²éƒ¨æ˜Žç¡®æ出:è¦ç»“åˆå„地实际,采用二代身份è¯çŽ°åœºæŠ¥å确认ã€çŽ°åœºé‡‡é›†ç…§ç‰‡å’ŒæŒ‡çº¹æˆ–é™è„‰ç‰ç”Ÿç‰©ç‰¹å¾ã€åŠæ—¶è¿›è¡Œä¿¡æ¯æ¯”对措施严防替考。通知采集照片和指纹或é™è„‰ç‰ç”Ÿç‰©ç‰¹å¾ã€åŠæ—¶è¿›è¡Œä¿¡æ¯æ¯”对措施严防替考。通知表明,指纹识别ã€äººè„¸è¯†åˆ«å’Œé™è„‰è¯†åˆ«ä¸‰ç±»æŠ€æœ¯æœ‰å¯èƒ½æˆä¸ºæœªæ¥é«˜è€ƒèº«ä»½æ ¸æŸ¥çš„强制手段。 早在2012年,河北çœæ•™è‚²è€ƒè¯•é™¢ä¸ºäº†è¿›ä¸€æ¥è§„范考试æµç¨‹ï¼Œå°±çŽ‡å…ˆåœ¨å›½å†…教育为了进一æ¥è§„范考试æµç¨‹ï¼Œå°±çŽ‡å…ˆåœ¨å›½å†…教育考试领域试点引入指纹识别技术。2016年,北京ã€å››å·ã€æ¹–北ã€å¹¿ä¸œç‰å¤šä¸ªçœä»½çš„高考采用人脸识别+指纹识别åŒé‡æŠ€æœ¯ç¡®è®¤è€ƒç”Ÿèº«ä»½ã€‚æ¯ä¸ªè€ƒç‚¹éƒ½é…å¤‡èº«ä»½æ ¸éªŒç»ˆç«¯ï¼Œè€ƒç”Ÿè¿›å…¥è€ƒåœºæ—¶éœ€è¦åœ¨è®¾å¤‡ä¸ŠåŒå®Œæˆåˆ·èº«ä»½è¯ã€æŒ‰æºæŒ‡çº¹ã€äººè„¸æ‹ç…§ï¼Œå¹¶ä¸”与之å‰æ³¨å†Œä¿¡æ¯è¿›è¡Œè”ç½‘æ¯”å¯¹ï¼Œä¸‰è€…æ ¸éªŒå‡é€šè¿‡æ‰èƒ½äºˆä»¥å‚åŠ é«˜è€ƒã€‚è€Œä»Ž2015年开始,蒙å¤è‡ªæ²»åŒºåœ¨é«˜è€ƒèº«ä»½æ ¸æŸ¥ä¸ä½¿ç”¨æŒ‡é™è„‰è¯†åˆ«æŠ€æœ¯ã€‚ 指纹识别率先打开了高考市场,紧éšå…¶åŽçš„是人脸。当å‰å’ŒæŒ‡çº¹è¯†åˆ«çŽ‡å…ˆæ‰“开了高考市场,紧éšå…¶åŽçš„是人脸。当å‰å’Œè¯†åˆ«ä¸¤ç±»æŠ€æœ¯å·²ç»åº”用于多çœçš„é«˜è€ƒèº«ä»½æ ¸æŸ¥ï¼ŒæŒ‡é™è„‰è¯†åˆ«ä¸¤ç±»æŠ€æœ¯å·²ç»åº”用于多çœçš„é«˜è€ƒèº«ä»½æ ¸æŸ¥ï¼ŒæŒ‡é™è„‰è¯†åˆ«æŠ€æœ¯è¿˜æœªå¤§èŒƒå›´åº”用。éšç€æ•™è‚²éƒ¨é€šçŸ¥çš„进一æ¥è½åœ°ï¼Œæ›´å¤šçœå°†åœ¨é«˜è€ƒä¸ä½¿ç”¨é™è„‰è¯†åˆ«æŠ€æœ¯ã€‚ 高考之外,自2015年起,å¸æ³•è€ƒè¯•åœ¨å„çœå„考区推行国家å¸æ³•è€ƒè¯•äººè„¸è¯†åˆ«ç³»ç»Ÿï¼Œè€ƒç”Ÿå¿…须先扫æ身份è¯å¹¶çŽ°åœºæ‹ç…§ï¼Œé€šè¿‡äººè„¸æ¯”对åŽæ–¹å¯è¿›å…¥è€ƒåœºã€‚2016年,部分地区的英è¯ç‰çº§è€ƒè¯•ä¹Ÿå¼•å…¥äº†äººè„¸è¯†åˆ«æŠ€æœ¯ã€‚高考之外å„类考试é€æ¸å¼•å…¥ç”Ÿç‰©è¯†åˆ«æŠ€æœ¯ï¼Œå°†æ”¾å¤§ç”Ÿç‰©è¯†åˆ«åœ¨æ•™è‚²éƒ¨é—¨çš„市场空间。 4.4ã€åŒ»ç–—部门:人脸识别带动智慧医疗新进展 2016å¹´3月,全国首家“人脸识别â€åŒ»ä¿æ”¯ä»˜ç³»ç»Ÿåœ¨æ¦æ±‰å¸‚ä¸å¿ƒåŒ»é™¢ä¸Šçº¿ï¼Œé€šè¿‡æ‰‹æœºåˆ·è„¸æ”¯ä»˜ï¼ŒåŒ»ä¿æ‚£è€…å¶æœ‰ä¸é€‚å¯ä»¥åœ¨å®¶é€šè¿‡ç½‘络院问诊,电å处方开具åŽï¼Œå¯ä»¥ç›´æŽ¥å®ŒæˆåŒ»ä¿è´¹ç”¨çš„缴纳,实现了医ä¿æ‚£è€…网上就诊,è¯å“快递到家。 人脸识别系统应用于医ä¿æ”¯ä»˜ç³»ç»Ÿï¼Œæ˜¯æ™ºæ…§åŒ»ç–—çš„æ–°çªç ´ã€‚ä¸è¿‡ç”±äºŽåˆ·è„¸æ”¯ä»˜æ¶‰åŠåŒ»ä¿è´¦æˆ·çº¿ä¸Šä½¿ç”¨çš„资金安全ç‰é—®é¢˜ï¼ŒæŠ€æœ¯èƒ½å¦åœ¨å›½å„大院推广还需涉åŠåŒ»ä¿è´¦æˆ·çº¿ä¸Šä½¿ç”¨çš„资金安全ç‰é—®é¢˜ï¼ŒæŠ€æœ¯èƒ½å¦åœ¨å…¨å›½å„大院推广,还需è¦çœ‹æ”¿åºœå±‚é¢ä¸‹ä¸€æ¥çš„支æŒåŠ›åº¦ã€‚ 5ã€æ¶ˆè´¹çº§åº”ç”¨ï¼šæ–¹å…´æœªè‰¾ï¼Œéœ€æ±‚ç«¯æ‰“å¼€å¥ å®šæœ€å¤§å¢žé•¿åŠ¨åŠ› 5.1ã€æ‰‹æœºç«¯æŒ‡çº¹è¯†åˆ«ï¼šæŒ‡çº¹è¯†åˆ«ç¡¬ä»¶ä»·è·Œé‡æ¶¨ï¼ŒNFC支付形æˆæ–°æŽ¨åŠ› 指纹识别产业链主è¦ç”±ç¡¬ä»¶çŽ¯èŠ‚和软件环节构æˆã€‚硬件环节包括指纹识别芯片ã€æŒ‡çº¹è¯†åˆ«æ¨¡ç»„,软件环节包括指纹识别方案ã€æ‰‹æœºç»ˆç«¯å’Œè½¯ä»¶åº”用。在硬指环节,从芯片到模组,还需ç»åŽ†å°è£…ã€coatingã€ç›–æ¿ã€é‡‘属环ç‰çŽ¯èŠ‚。 éœ€æ±‚æ‰©å¤§å’Œä»·æ ¼æˆæœ¬ä¸‹é™æŽ¨åŠ¨æŒ‡çº¹æ¨¡ç»„出货é‡é«˜é€Ÿä¸Šå‡ã€‚è¿‘å¹´æ¥ï¼Œæ™ºèƒ½æ‰‹æœºå’Œç§»åŠ¨æ”¯ä»˜éœ€æ±‚çš„æ‰©å¼ å¸¦åŠ¨äº†æ‰‹æœºç«¯æŒ‡çº¹è¯†åˆ«æŠ€æœ¯éœ€æ±‚çš„å¢žé•¿ã€‚åŒæ—¶ï¼ŒæŒ‡çº¹è¯†åˆ«é€æ¸æˆä¸ºä¸é«˜ç«¯æ——èˆ°æœºåž‹çš„æ ‡é…,且在低端åƒå…ƒå¸‚场的普åŠçŽ‡å‰§å¢žã€‚两方é¢å› ç´ å åŠ ï¼ŒæŽ¨åŠ¨æŒ‡çº¹æ¨¡ç»„çš„éœ€æ±‚ä¸æ–æ‰©å¼ ã€‚è€Œéšç€ä¸å›½æœ¬åœŸåŽ‚商全é¢è¿›å…¥è¯†åˆ«å¸‚åœºå¹¶åŠ å¿«æŽ¨å‡ºäº§å“ï¼ŒæŒ‡çº¹è¯†åˆ«æ¨¡ç»„ä»·æ ¼è¿›å…¥ä¸‹è¡Œé€šé“ã€‚æŒ‡çº¹æ¨¡ç»„çš„ä»·æ ¼2014年底约为10美元,2015å¹´é™è‡³5美元,目å‰å¸‚场å‡ä»·åœ¨3-4美元/ç‰‡ã€‚éœ€æ±‚çš„æ‰©å¼ å’Œä»·æ ¼çš„ä¸‹è¡Œå¸¦æ¥æŒ‡çº¹æ¨¡ç»„出货é‡å¿«é€Ÿå¢žé•¿ã€‚2016年上åŠå¹´ï¼ŒæŒ‡çº¹æ¨¡ç»„的出货é‡å‘ˆçŽ°é€æœˆå¢žé•¿çš„趋势,上åŠå¹´å‡ºè´§æ€»è¾¾åˆ°1.51亿(ä¸è®¡ç®—苹果手机的指纹模组)。我们ä¿å®ˆä¼°è®¡2016年整年的出货总é‡ä¸º3亿,å‡è®¾å‡ä»·ä¸º3美元,2016年整年指纹模组的销售é¢å°†è¾¾åˆ°9亿美元。 æ®æŽ¥è¿‘FPC的业内资深人士分æžç§°ï¼Œä»Šå¹´æŒ‡çº¹è¯†åˆ«æ¸—é€çŽ‡ä¸º20%-25%。如果指纹识别渗é€çŽ‡å¯ä»¥è¾¾åˆ°50%的水平,指纹芯片ã€æ¨¡ç»„市场规模将实现翻å€å¢žé•¿ã€‚ NFC支付相继推出,移动æˆä¸ºæ‰‹æœºæŒ‡çº¹è¯†åˆ«å…³é”®åº”用场景。2013å¹´9月,苹果推出首款æè½½æ£é¢æŒ‰åŽ‹å¼æŒ‡çº¹è¯†åˆ«ï¼ˆTouchID)的手机iphone5s,支æŒè§£é”/支付ã€ä¸ŽHome键完美èžåˆã€‚自iPhone5s之åŽï¼Œå…¨ä¸–界的高端旗舰手机都开始攻关指纹识别技术,指纹识别在消费级市场迎æ¥äº†çˆ†å‘å¼å¢žé•¿ã€‚手机端指纹识别的应用场景包括:å±å¹•è§£é”ã€å¯¹æ‰‹æœºçš„文件或者应用场景包括:å±å¹•è§£é”ã€å¯¹æ‰‹æœºçš„文件或者appè¿›è¡ŒåŠ å¯†ã€åº”用互动(æ¯”å¦‚é•¿æŒ‰æŒ‡çº¹ä¼ æ„Ÿå™¨ç»™é¢„å…ˆè®¾å®šçš„äººæ‰“ç”µè¯ï¼ŒåŒå‡»ä¼ 感器就能共享照片,打开æ’æ”¾å™¨çš„æ—¶å€™åœ¨ä¼ æ„Ÿå™¨ä¸Šå‘å³æ»‘动就能切æ¢ä¸‹ä¸€é¦–æŒç‰)以åŠè‡ªå®¶æœåŠ¡(å„手机厂商独特的指纹解é”æœåŠ¡ï¼Œä¾‹å¦‚åŽä¸ºçš„应用é”ã€OPPON3çš„æ‹ç…§ç‰æ–¹é¢)。而éšç€ç¬¬ä¸‰æ–¹æ”¯ä»˜å·¥å…·å’Œæ‰‹æœºé“¶è¡Œé€æ¸æ”¯æŒæŒ‡çº¹è¯†åˆ«ï¼Œç§»åŠ¨æ”¯ä»˜å¼€å§‹æˆä¸ºæ‰‹æœºæŒ‡çº¹è¯†åˆ«çš„主è¦åº”用场景。å¦å¤–,三星ã€åŽä¸ºã€ä¸å…´ã€å°ç±³ç‰åŽ‚商相继与银è”è¾¾æˆåˆä½œï¼ŒæŽ¨å‡ºNFC支付。NFC支付å¯åœ¨ä¸è”网的状æ€ä¸‹å®Œæˆï¼Œä¸Žæ‰‹æœºç¡¬ä»¶çš„结åˆæ›´åŠ å®Œå–„ï¼Œä¸”ç”±äºŽå…¶ä¿¡ç”¨åŠ å¯†ç‰å®‰å…¨åŠŸèƒ½é›†æˆåœ¨ç¡¬ä»¶ä¸Šï¼Œå®‰å…¨æ€§æ›´é«˜ã€‚NFC支付在分割当å‰ç§»åŠ¨æ”¯ä»˜å˜é‡å¸‚场的åŒæ—¶ï¼Œæœ‰æœ›å‡å€Ÿå…¶ä¼˜åŠ¿æ’¬åŠ¨ä¸€éƒ¨åˆ†å¢žé‡å¸‚场,这将对指纹识别芯片ã€æ¨¡ç»„和指纹识别软件环节形æˆæ‹‰åŠ¨ä½œç”¨ã€‚ 5.2ã€æ‰‹æœºç«¯è™¹è†œè¯†åˆ«ï¼šæ£å¤„产业化åˆçº§é˜¶æ®µï¼Œé«˜ç«¯æœºå˜åœ¨ç©ºé—´ 2015å¹´5月,富士通推出了全çƒé¦–款æ载虹膜识别技术的新款机型ArrowsNXF-04G,用户åªè¦çŸæš‚å‡è§†è§¦æŽ§å±ä¾¿å¯è‡ªåŠ¨è§£é”,并能够实现è´ä¹°APPçš„è´¦å·è¾“入或具备登陆网页的密ç 功能。三星今年的旗舰机型GalaxyNote7支æŒè™¹è†œæ‰«æ,用于解é”çš„åŒæ—¶ï¼ŒSamsungPay也获得了对于虹膜扫æ功能的支æŒã€‚而å³å°†å‘布的åŽä¸ºå¹´åº¦æ——舰Mate9æ®ç§°ä¹Ÿå°†å†…置虹膜识别功能。 è™¹è†œè¯†åˆ«ç®—æ³•å›½å¤–é¢†å…ˆï¼Œå›½å†…è¿›å…¥äº§ä¸šåŒ–é˜¶æ®µã€‚è™¹è†œè¯†åˆ«æŠ€æœ¯çš„æ ¸å¿ƒçŽ¯èŠ‚æ˜¯ç®—æ³•ã€‚åœ¨è¯¥çŽ¯èŠ‚ï¼Œå›½é™…é¢†å…ˆçš„åŽ‚å•†æœ‰ç¾Žå›½Iridianã€Iriteck和韩国Jirisç‰ã€‚美国Iridianå…¬å¸æ˜¯å…¨çƒæœ€å¤§çš„专业虹膜识别技术和产å“æ供商,它和Irisguardã€Securimetricsã€LGã€æ¾ä¸‹ã€OKIã€NECç‰å…¬å¸è¿›è¡Œåˆä½œï¼Œä»¥æŽˆæƒæ–¹å¼æä¾›è™¹è†œè¯†åˆ«æ ¸å¿ƒç®—æ³•ï¼Œæ”¯æŒåˆä½œä¼™ä¼´ç”Ÿäº§è™¹è†œè¯†åˆ«ç³»ç»Ÿã€‚Iritechæä¾›æ ¸å¿ƒè½¯ä»¶ä»¥åŠé•œå¤´ï¼Œç”±å…¶ä»–å…¬å¸åœ¨æ¤åŸºç¡€ä¸Šå¼€å‘应用系统,并且负责销售。目å‰ï¼Œå›½å†…çš„è™¹è†œè¯†åˆ«æ ¸å¿ƒç®—æ³•å¤„äºŽèµ·æ¥é˜¶æ®µï¼ŒæŠ€æœ¯æ供商主è¦æ˜¯ä¸Šæµ·äº¤å¤§å›¾åƒæ‰€å’Œä¸ç§‘é™¢è‡ªåŠ¨åŒ–æ‰€ï¼Œå…¶è™¹è†œç ”ç©¶æˆæžœå·²ç»äº§ä¸šåŒ–,主è¦ç”±ä¸ç§‘虹霸和èšè™¹å…‰ç”µè¿™ä¸¤å®¶å…¬å¸è¿›è¡Œè¿è¥ã€‚ç›®å‰ï¼Œä¸¤å®¶å…¬å¸çš„产å“å·²ç»åœ¨å•†ä¸šå’Œå…¬å…±é¢†åŸŸèŽ·å¾—了应用,未æ¥æœ‰æœ›æ‹“展到消费级的手机端。 大é‡é»‘è‰²è™¹è†œæ ·æœ¬ä¸ºå›½å†…ç ”å‘æ供契机。当å‰ï¼Œå›½å†…è™¹è†œæŠ€æœ¯çš„å…³é”®ç ”å‘æ–¹å‘是针对东方人的黑色虹膜识别。相对于西方人的虹膜,黑色虹膜颜色更深,纹ç†åŒºåŸŸæ›´ç‹çª„,纹ç†æ•°é‡æ›´å°‘,而且普éå˜åœ¨æ¯”较严é‡çš„眼ç‘或ç«æ¯›é®æŒ¡ï¼Œè¿™äº›ç‰¹ç‚¹å¯¼è‡´ä¸€èˆ¬çš„虹膜识别技术在应用于东方人时识别精度会大大下é™ï¼Œç”šè‡³æˆä¸ºè™¹è†œè¯†åˆ«æŠ€æœ¯åœ¨ä¸œæ–¹äººç¾¤ä¸æ‰©å¤§åº”用的潜在障ç¢ã€‚ä¸å›½æ‹¥æœ‰æœ€å¤§çš„é»‘è‰²è™¹è†œæ ·æœ¬ï¼Œè¿™å°†ä¸ºå›½å†…ç ”ç©¶æœºæž„å’ŒåŽ‚å•†æä¾›å¥‘æœºï¼Œåœ¨è¯¥ç ”å‘æ–¹å‘上实现赶超。 指纹识别å¯å¤åˆ¶çš„特性一定程度上削弱了它的安全性。而ä¸é«˜ç«¯æ‰‹æœºç”¨æˆ·å¯¹æ‰‹æœºæ•°æ®ä¿å¯†æ€§å’Œæ”¯ä»˜å®‰å…¨æ€§çš„è¦æ±‚æžé«˜ï¼Œå› 而,虹膜识别技术在ä¸é«˜ç«¯æœºåž‹ä¸Šå˜åœ¨å¸‚场空间。 5.3ã€æŒ‡çº¹é”:渗é€çŽ‡å°šä½Žï¼Œä½œä¸ºæ™ºèƒ½å®¶å±…å…¥å£ä¼˜åŠ¿æ˜Žæ˜¾ 指纹ã€æ™ºèƒ½é”应用。指纹é”是将电å技术ã€é›†æˆç”µè·¯è®¾è®¡ã€å¤§é‡çš„电å元器件,结åˆè®¡ç®—机网络技术ã€å†…置软件å¡ã€ç½‘络报è¦ã€é”体的机械设计ã€ç”Ÿç‰©è¯†åˆ«ç‰å¤šç§åˆ›æ–°çš„识别技术的综åˆäº§å“。 ç›®å‰æŒ‡çº¹é”在国内渗é€çŽ‡è¾ƒä½Žã€‚国内指纹é”市场至今已ç»è¿‡äº†10多年的漫长培育。从2012年开始,指纹é”产å“处于高速增长的阶段,2015年比2014年增长了82%,但目å‰æ¸—é€çŽ‡ä»ç„¶è¾ƒä½Žã€‚以往在ä¸å›½æ™ºèƒ½é”主è¦è¢«ç”¨äºŽé«˜ç«¯é…’店ã€å…¬å¯“与别墅当ä¸ï¼Œåœ¨æ™®é€šå®¶åºç”¨æˆ·æ™®åŠçŽ‡ä¸åˆ°2%,而在欧美ç‰è¥¿æ–¹å‘达国家智能é”的市场,而在欧美ç‰è¥¿æ–¹å‘达国家智能é”的市场,å 有率在50%以上,日本ã€éŸ©å›½æ™ºèƒ½é”æ›´å 民用é”70%以上的市场。 è¿‘å¹´æ¥ï¼Œåœ¨æ™ºèƒ½å®¶å±…系统ä¸ï¼ŒæŒ‡çº¹é”有ç€ç‹¬ç‰¹çš„应用场景与集æˆç©ºé—´ã€‚ä¼´éšæ™ºèƒ½å®¶å±…功能延伸与智硬件创业浪潮,指纹é”开始æˆä¸ºé‡è¦çš„应用è½åœ°ç‚¹ã€‚然而与之å‰ç›¸æ¯”,目å‰å¸‚场情况å¯èƒ½å‡ºçŽ°äº†ä»¥ä¸‹å˜åŒ–:目å‰å¸‚场情况å¯èƒ½å‡ºçŽ°äº†ä»¥ä¸‹å˜åŒ–: (1)去ä¸é—´åŒ–销售:在2015年之å‰ï¼ŒæŒ‡çº¹é”产å“的零售价基本在三åƒå…ƒä»¥ä¸Šï¼Œéƒ¨åˆ†å“牌å¯ä»¥è¾¾åˆ°å››åƒå…ƒä»¥ä¸Šã€‚éšç€åˆ›æ–°åž‹ä¼ä¸šè¿›å…¥æŒ‡çº¹é”领域,从2016年开始,很多智能家居å“牌也延伸到这一领域,å†åŠ 上互è”网å“牌的新è¿ä½œæ–°æ¨¡å¼åŠ©æŽ¨ï¼Œéƒ¨åˆ†åšåˆ°äº†åŽ»ä¸é—´åŒ–ï¼Œåœ¨ä»·æ ¼ä¸Šæœ‰æ‰€ä¸‹é™ã€‚å¦å¤–,大é‡ä¼ä¸šè¿›å…¥æŒ‡çº¹é”å¸‚åœºï¼ŒåŠ é€Ÿè¡Œä¸šæ™®åŠï¼Œå¯¹ä¼ 统ä¼ä¸šçš„äº§ä¸šé“¾ä½“ç³»ä¼šé€ æˆå†²å‡»ã€‚éšç€æŠ€æœ¯å’Œç”Ÿäº§é—¨æ§›è¿›ä¸€æ¥é™ä½Žï¼Œå„个生产厂家出现竞争现象,压缩了æˆæœ¬ã€‚ (2)整体产å“设计能力的æå‡ï¼šåŒ…括与门厂和å”ä½åŒ¹é…兼容性的æå‡ã€‚以å‰æŒ‡çº¹é”和门厂的设计相互都没有贴åˆï¼Œè¿™å°±å¯¼è‡´æŒ‡çº¹é”到门厂去需è¦ç»è¿‡æ¯”较å¤æ‚的安装调试,安装调试和销售维护的æˆæœ¬éƒ½æ¯”较高。现在指纹é”和门厂在技术上形æˆäº†è”通,指纹é”çš„å®‰è£…æ ‡å‡†éµå¾ªç€é—¨åŽ‚çš„æ ‡å‡†ï¼Œå„æ–¹é¢çš„æˆæœ¬éƒ½ä¼šé™ä½Žã€‚ (3)指纹识别和嵌入å¼å•ç‰‡æœºæŠ€æœ¯çš„æˆç†Ÿï¼šåŒ…括芯片æˆæœ¬çš„é™ä½Žï¼Œè¿™ä¼šè®©æŒ‡çº¹é”产å“进一æ¥ç¨³å®šï¼ŒæŽ¨åŠ¨è¡Œä¸šå‘展。 (4)智能家居和物è”网技术的æˆç†Ÿï¼šæ™ºèƒ½å®¶å±…和物è”网技术的æˆç†Ÿï¼šè®©æŒ‡çº¹é”èžå…¥åˆ°äº†æ™ºèƒ½å®¶å±…æ•´ä½“çš„èŒƒç•´ã€‚æ™ºèƒ½å®¶å±…åœ¨å®£ä¼ æŽ¨å¹¿æ–¹é¢å¯ä»¥è®©æ¶ˆè´¹è€…快速认识指纹é”ï¼Œæœ‰çŸ¥å°±ä¼šæ™ºèƒ½å®¶å±…åœ¨å®£ä¼ æŽ¨å¹¿æ–¹é¢å¯ä»¥è®©æ¶ˆè´¹è€…快速认识指纹é”,有知就会费和普åŠã€‚ (5ï¼‰ä½¿ç”¨è€…æ¶ˆè´¹ä¹ æƒ¯æ”¹å˜ï¼š 过去ä½å®…ç‰çš„主è¦è´ä¹°è€…多为70åŽï¼Œæ²¡æœ‰å½¢æˆæŒ‡çº¹è¯†åˆ«çš„ä¹ æƒ¯ï¼Œè€Œç›®å‰è´æˆ¿è€…ä¸å¼€å§‹å‡ºçŽ°80甚至90åŽï¼Œè¿™ä¸€éƒ¨åˆ†æ¶ˆè´¹ç¾¤ä½“由于iphoneç‰æ™ºèƒ½æ‰‹æœºçš„ä½¿ç”¨ä¹ æƒ¯åŸ¹å…»ï¼Œå¯¹äºŽæŒ‡çº¹è¯†åˆ«å·²ç»è¾ƒä¸ºç†Ÿæ‚‰ï¼Œæ›´æ„¿æ„在ä½å®…ä¸æŽ¥å—指纹é”。 从“指纹é”â€åˆ°â€œæ™ºèƒ½é”â€ï¼šåœ¨æŒ‡çº¹åŠ 密外,近年æ¥æ–°åž‹æ™ºèƒ½é”还能åšåˆ°APPå‘çŸä¿¡ã€äº‘è”网报è¦ï¼Œä½¿å¾—智能é”的安全级别大大高于机械é”ï¼Œæ‰‹æŒ‡æŒ‡çº¹ä»£æ›¿äº†ä¼ ç»Ÿé’¥åŒ™ï¼Œäº§å“体验也更便æ·ã€‚ 与其他众多智能家居硬件相比,指纹é”作为入å£æœ‰å¾—天独厚优势:智能é”çš„æ›´æ¢å‘¨æœŸä¸º5-8年,相比于其它智能家居使用频次高,更周期长,智能化æˆæœ¬è¾ƒä½Žã€‚åŒæ—¶æ™ºé”以个人指纹作为IDå¯ä»¥è¿žæŽ¥å…¶ä»–智能家居硬件,具备生æ€é“¾çš„纵深潜力; 在新的市场环境下,指纹é”ã€æ™ºèƒ½é”创业项目迎æ¥äº†æŠ•èžèµ„的春天:知å智能é”å“牌第å‰å°”ã€è€¶é²è¢«ç‘žå…¸é”具巨头亚è¨åˆèŽ±æ”¶è´ï¼Œè¡Œä¸šèµ„æºæ•´åˆåŠ›åº¦åŠ 剧。国内项目,å°å˜€äº‘智能é”于2016å¹´3月获得Aè½®1.23亿人民å¸èžèµ„,代表ç€æ™ºèƒ½å®¶å±…çš„çªç ´ç‚¹æ£ä»Žæ™ºèƒ½å®¶ç”µå‘智能安防领域转移的趋势。 ç›®å‰ï¼Œæ™ºèƒ½é”市场潜力巨大。éšç€ä¸å›½äººå£åŸºæ•°æ‰©å¤§ã€æ–°å»ºæ¥¼ç›˜å¢žå¤šã€æ¥¼ä»·æ€»ä½“水平上å‡ã€å›½äººå¯¹å±…ä½æ¡ä»¶çš„è¦æ±‚æ高,目å‰ï¼Œå›½å†…一线ã€äºŒçº¿åŸŽå¸‚房价ä¸æ–上涨,如果æ¯å¹³ç±³å”®ä»·10000元以上,那么指纹é”çš„æˆæœ¬å¹³æ‘Šåˆ°æ¯å¹³ç±³ä»·æ ¼ä¸Šï¼Œæ€»ä»·ä¸Šæ¶¨å¹…度基本å¯ä»¥å¿½ç•¥ã€‚å› æ¤ï¼Œè¶Šæ¥è¶Šå¤šçš„房开商采用指纹é”æ¥å¸å¼•æ¶ˆè´¹è€…。åŒæ—¶è¿˜æœ‰å¯¹é«˜ç§‘技的çƒè¡·ã€ç¤¾ä¼šä¸ç¨³å®šå› ç´ å¸¦æ¥çš„安防问题,使指纹é”市场é€æ¸æ‰©å¤§ã€‚æ ¹æ®åŽç»è§†ç‚¹å¯¹ç‰©ç†é—¨ç¦æŽ§åˆ¶å¸‚åœºçš„è°ƒæŸ¥ç ”ç©¶è¡¨æ˜Žï¼Œè¶…è¿‡70%的最终用户和80%的行业å—访者认为,在未æ¥3至5年内,他们希望以手机ã€é’¥åŒ™ç‰Œã€æ ‡ç¾æˆ–å‡è¯å¡ç‰æ–¹å¼æ›¿ä»£çŽ°åœ¨çš„ä¼ ç»Ÿé—¨é”。目å‰æˆ‘国全国城镇ä½å®…在3.4亿套左å³ï¼Œå‡è®¾æœ‰ä¸€åŠèƒ½å®žçŽ°æ™ºèƒ½é”渗é€ï¼Œæ¯æˆ·ä½¿ç”¨æ™ºèƒ½ç”Ÿç‰©è¯†åˆ«é”1.5个,那智能é”的需求é‡å¯ä»¥è¾¾åˆ°2.55亿个。按照æ¯ä¸ªæ™ºèƒ½é”2000å…ƒçš„ä»·æ ¼è®¡ç®—ï¼Œæ€»å¸‚åœºè§„æ¨¡å¯ä»¥è¾¾åˆ°5100亿元。 6ã€å¹¿é˜”市场和多ç§ç›ˆåˆ©æ¨¡å¼å¸¦æ¥å·¨å¤§åˆ©æ¶¦ç©ºé—´ 6.1ã€ä»Žç¡¬ä»¶é”€å”®åˆ°æ•°æ®å˜çŽ°ï¼Œç›ˆåˆ©æ¨¡å¼å¤šæ · 生物识别盈利模å¼è¾ƒä¸ºå¤šæ ·åŒ–:我们认为盈利模å¼å¯ä»¥åˆ†ç¡¬ä»¶é”€å”®ï¼Œè½¯ä»¶ã€è§£å†³æ–¹æ¡ˆæœåŠ¡æ供,云æœåŠ¡æ供,未æ¥å¯èƒ½çš„æ•°æ®å˜çŽ°å‡ ç§ã€‚(1)硬件销售。硬件是生物识别的入å£ï¼Œç¡¬ä»¶é”€å”®ä¹Ÿæ˜¯ç”Ÿç‰©è¯†åˆ«é¢†åŸŸæœ€åŸºç¡€çš„盈利模å¼ã€‚æ供优秀的硬件,是生物识别领域公å¸ä¸€ç§è¾ƒä¸ºä¼ 统的盈利途径。 例如虹膜识别,由于æå–眼白毛细血管信æ¯çš„过程容易å—åˆ°å…‰çº¿çš„å¹²æ‰°ï¼Œå› æ¤é¦–先需è¦ä½¿ç”¨è¿‘红外LEDæ¥æ供照射光线,需è¦ä½¿ç”¨å››å…ƒæ™¶ç²’机å°è®¾å¤‡ï¼Œè¿™ä¸€æŠ€æœ¯éš¾åº¦è¾ƒå¤§ï¼Œä¸»è¦çº¢å¤–线LED厂商包括日本EPITEXã€æ¬§æ´²åŽ‚商欧å¸æœ—ã€å°æ¹¾çš„æ™¶ç”µå’Œç ”æ™¶ã€‚åŒæ—¶ï¼Œæå–ä¿¡æ¯éœ€è¦å°åž‹æ‘„åƒå¤´æ¨¡ç»„(CCM),它将光å¦å›¾åƒè½¬åŒ–为电å视频信å·çš„装臵,其åŽç”µåä¿¡å·å°†è¢«è½¬åŒ–为于数ç å½±åƒè®¾å¤‡ä¹‹æ˜¾ç¤ºå±ä¸Šï¼Œä»¥ä¾›ä½¿ç”¨è€…将其储å˜ä¸ºæ•°ç å½±åƒã€‚ 例如指纹识别。æ¯ä¸€æ¬¡çš„指纹解é”ç»åŽ†ä¸‰ä¸ªè¿‡ç¨‹ï¼Œé¦–å…ˆä¼ æ„Ÿå™¨æ£€æµ‹åˆ°æ‰‹æŒ‡æŒ‰ä¸‹å¹¶åˆ¤æ–æ‰‹æŒ‡è¦†ç›–ä¼ æ„Ÿå™¨é¢ç§¯è¾¾åˆ°éªŒè¯çš„æ ‡å‡†ï¼Œå…¶æ¬¡è¿›è¡ŒæŒ‡çº¹æ•°æ®éªŒè¯ï¼Œæœ€åŽéªŒè¯é€šè¿‡ç‚¹äº®å±å¹•å¹¶è§£é”å±å¹•ï¼Œæ¯ä¸€ä¸ªè¿‡ç¨‹éƒ½ä¾èµ–于硬件本身的处ç†èƒ½åŠ›ï¼Œå› æ¤ç¡¬ä»¶åœ¨æ•´ä¸ªæŒ‡çº¹è¯†åˆ«äº§ä¸šé“¾ä¸å 有æžé«˜åœ°ä½ã€‚在整个指纹识别产业ä¸ï¼ŒèŠ¯ç‰‡ä»·å€¼å 比æžé«˜ï¼Œå 整个模组的70%ï¼›åˆåˆ†ä¸ºIC设计ã€æ™¶åœ†åˆ¶é€ ã€å°æµ‹ä¸‰ä¸ªçŽ¯èŠ‚,在我国A股上市公å¸ä¸ï¼Œç¡•è´å¾·ã€æ™¶æ–¹ç§‘技ç‰å…¬å¸éƒ½å…·æœ‰ä¸€å®šçš„å°è£…和模组技术实力。 (2)软件ã€è§£å†³æ–¹æ¡ˆæœåŠ¡æ供。优秀的软件技术有助于é™ä½Žè¯†åˆ«é”™è¯¯çŽ‡ï¼Œæ高 识别效率,是生物识别ä¸çš„æ ¸å¿ƒçŽ¯èŠ‚ï¼Œç‰¹åˆ«åœ¨äººè„¸è¯†åˆ«ã€å£°çº¹è¯†åˆ«ã€æ¥æ€è¯†åˆ«ç‰å¯¹äºŽç®—法è¦æ±‚较高的领域。专注软件和平å°å¼€å‘çš„å…¬å¸å°†æœ€å—益于该类领域。 例如人脸识别。目å‰å·²æœ‰å¤šå®¶å…¬å¸åœ¨äººè„¸è¯†åˆ«è§£å†³æ–¹æ¡ˆé¢†åŸŸå¸ƒå±€ã€‚例如å·å¤§æ™ºèƒœï¼Œå…¬å¸ä¸‰ç»´äººè„¸è¯†åˆ«æŠ€æœ¯é‡‡ç”¨â€œä¸‰ç»´å»ºåº“,二维识别â€çš„æ–¹å¼ï¼ŒæŠ•å…¥å°ã€ç²¾åº¦é«˜ï¼Œå…·æœ‰æ˜Žæ˜¾çš„技术优势。该系统已ç»å¼€å§‹è¯•ç‚¹åº”用。佳都科é‡ç‚¹å¸ƒå±€çš„是云从科技公å¸çš„人脸识别技术,目å‰ç ”å‘的多项产å“进入了试点和应用阶段未æ¥ï¼Œå…¬å¸è¿˜å°†è¿›ä¸€æ¥åŠ 大对人脸识别ç‰å›¾å½¢å›¾åƒæ™ºèƒ½åˆ†æžæŠ€æœ¯çš„æŠ•å…¥åŠ›åº¦ï¼ŒåŠ å¿«äº§å“化和产业化进程,å‘国际领先的技术水平迈进。除æ¤ä»¥å¤–,东方网力ã€æµ·åº·ç‰ä¸Šå¸‚å…¬å¸å·²ç»åœ¨è§†é¢‘管ç†ã€äººè„¸è¯†åˆ«é¢†åŸŸæœ‰è¾ƒå¼ºçš„技术优势和稳固的市场地ä½ã€‚ 云æœåŠ¡æ¨¡å¼ã€‚除了直接æ供解决方案或软件外,部分生物识别公å¸è¿˜åº”用云模å¼æä¾›æœåŠ¡ã€‚例如旷视科技应用PaaS模å¼ï¼Œæ‰“é€ æ™ºèƒ½è§†è§‰äº‘æœåŠ¡ï¼Œé€šè¿‡å‘下游客户æ供人脸或者图åƒè¯†åˆ«çš„æœåŠ¡æ¥èŽ·å¾—收入。例如,美图秀秀就是旷视科技“人脸识别云æœåŠ¡â€çš„客户,美图秀秀ä¸ç”¨è‡ªå·±å¼€å‘相应的人脸识别模å—,åªéœ€è¦æŽ¥å…¥æ—·è§†ç§‘技æ供的API和离线引擎就å¯ä»¥äº«å—现æˆçš„人脸检测ã€åˆ†æžå’Œè¯†åˆ«ç‰æœåŠ¡ã€‚è¿™ç§æ¨¡å¼åŒºåˆ«äºŽä¼ 统的项目制,具有éžå¸¸å¥½çš„盈利å‰æ™¯ã€‚ æžè§†è§’科技是一家计算机视觉åŠå¤§æ•°æ®åˆ†æžå…¬å¸ï¼Œæ˜¯ä¸€å®¶PaaSå¹³å°æ供商。公å¸é€šè¿‡å¼€æ”¾äº‘端平å°ï¼Œä¸ºç®—法开å‘者æ供开å‘环境ã€æµ·é‡æ•°æ®ã€æž¶æž„支æŒç‰ä¼˜è´¨ç®—法和解决方案。 (3)大数æ®å˜çŽ°ã€‚计算机公å¸é™¤äº†æ供软件工具与æœåŠ¡ï¼Œè¿˜æœ‰å¯èƒ½é€šè¿‡ä¸Žå®¢æˆ·çš„åˆä½œï¼Œå…±åŒå®žçŽ°å®¢æˆ·æ•°æ®çš„å˜çŽ°ï¼Œæ‹“展新的商业模å¼ã€‚ 例如指纹识别领域。作为åªèƒ½å®¶å±… Intellective Electric Meter,Industrial Electric Meter,General Electric Meter,Electro Industries Meters Yuyao Gongyi Meter Co.,Ltd. , https://www.yycj.com